11 Which of the Following Are Breach Prevention Best Practices
Train employees on data security practices and awareness. When a data breach occurs involving a cloud service the impulsive reaction is to denounce using the cloud at least for sensitive information.

The Cost Of A Data Breach In 2021 Endpoint Protector
S3 Breach Prevention.

. You might also consider the following recommendations. Breach prevention strategies TheftLoss. What are breach prevention best practices.
Best Practices for Incident Response Plans The First 24 Hours Following a Breach Questions Reputation. Access only the minimum amount of PHIpersonally identifiable information PII necessary. Best Practices in Breach Prevention Develop appropriate security measures Monitor compliance with required measures Comply with reporting requirements W.
2 Data Breach Landscape Data breaches cost companies an average of 221 per compromised record. Organizational leaders know this. 20 Which of the following are breach prevention best practices.
Logoff or lock your workstation when it is unattended. Logoff or lock your workstation when it is unattended C. Regular backups of your most sensitive data should be a part of this IRP to help you mitigate the damages a data breach could cause to business functions.
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended. Regularly monitor networks and databases for unusual traffic. The following are breach prevention best practices.
Since cloud security is not widely understood it may be difficult to delineate it in the context of more general information security. Ideally if your company is dealing with sensitive data then you should perform vulnerability scans every week. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
Perform suspicious email training exercises to help employees identify potentially nefarious emails. Select the best answer. What are breach prevention best practices.
See answer 1 Best Answer. 1 who has lead responsibility. Promptly retrieve documents containing PHIPHI.
Discuss best practices for preventing breaches. One of the most common causes of a data breach is weak password policies. Which of the following are breach prevention best practices.
These 15 best practices can be used to reduce the likelihood of a data breach and help you respond more quickly to an attack. 2 Which of the following are breach prevention best practices. Logoff or lock your workstation when it is unattended.
You should always logoff or lock your workstation when it. Organizations should perform the scans on every system on their network both external and internal. 13 Best Practices You Should Implement.
Conduct a Risk Assessment. Companies should develop data breach response plans and educate the entire organization on proper protocol in the event of a breach. Out of the box AWS offers.
11 Which of the following are breach prevention best practices. Of the 71 reported incidents from Jan. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above correct 3 The minimum necessary standard.
All of the above. Which of the following are breach prevention best practices. Logoff or lock your workstation when it is unattended C.
3-June 11 only 18. Invest in up-to-date data loss prevention DLP technology. This plays a pivotal role in protection against data breaches.
A- Access only the minimum amount of PHIpersonally identifiable information PII necessary. Data breaches are a reality that all businesses need to take seriously. Promptly retrieve documents containing PHIPHI from the printer.
Knowing your vulnerabilities is only part of the solution. Promptly retrieve documents containing PHIPHI from the printer D. You and your key stakeholders should be prepared with an incident response plan that defines roles responsibilities and protocol so.
Access only the minimum amount of PHIpersonally identifiable information PII necessary B. Access only the minimum amount of PHIpersonally identifiable information PII necessary. However according to a new breach response best practices survey from ID Experts the majority of respondents want to do the right thing by their customers when it comes to breach response.
Promptly retrieve documents containing PHIPHI from the printer. Access only the minimum amount of phipersonally identifiable information pii necessary logoff or lock your workstation when it is unattended promptly retrieve documents containing phiphi from the. Data breaches are an everyday reality in a connected business world.
Data Breach Prevention. Access only the minimum amount of PHIpersonally identifiable information PII necessary B. The following are breach prevention best practices.
Logoff or lock your workstation when it is unattended. The following best practices may help. 11 Critically the plan should be actionablemeaning that it should provide specific concrete procedures to follow in the event of a cyber incident 12 At a minimum procedures should address.
Do you have strong password policy and is it being adhered to. B- Logoff or lock your workstation when it is unattended. Best Practices for Enterprise Cloud Security.
All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary and by promptly retrieving documents containing PHIPII from the printer. HIPAA and Breach Prevention. Top 10 Best Practices for Handling a Data Breach.
Sensitive data about identity collected stored transmitted or processed. Password policies that include regular rotation and high levels of. 3 2015 Definitions.

7 Best Practices For Third Party Security Risk Management Ekran System

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

How To Prevent Cyber Attacks Top Ways To Protect Yourself Maryville Online
7 Data Loss Prevention Best Practices Expert Explains Purplesec
Passwordless Authentication Options And Best Practices

Official 2022 Hipaa Compliance Checklist
7 Data Loss Prevention Best Practices Expert Explains Purplesec
Penetration Test Steps 5 Phases And Process

7 Data Loss Prevention Best Practices Expert Explains Purplesec
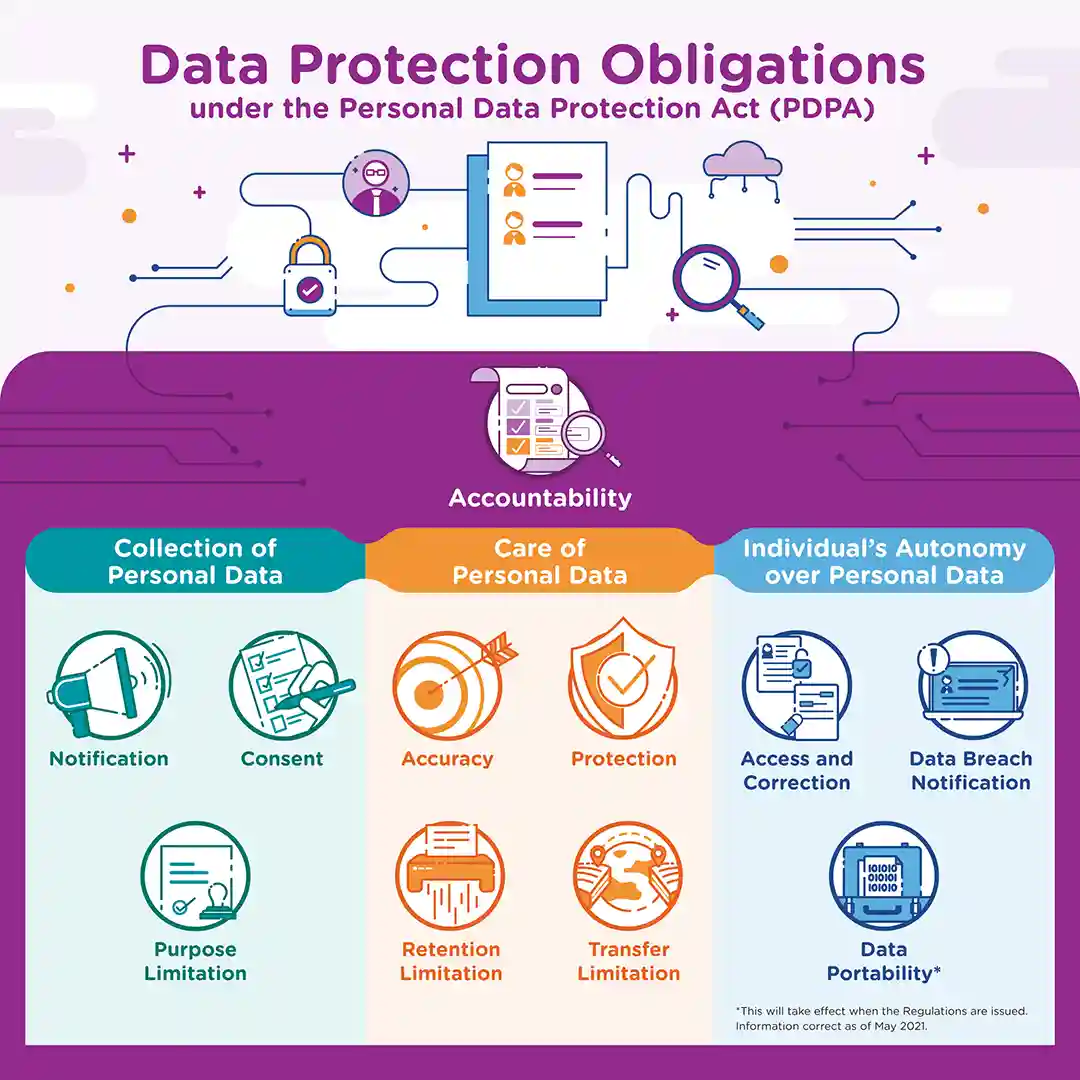
Pdpc Data Protection Obligations

Enterprise Data Breach Causes Challenges Prevention And Future Directions Cheng 2017 Wires Data Mining And Knowledge Discovery Wiley Online Library

Cyber Crime Investigation Making A Safer Internet Space

Data Breach Response Times Trends And Tips

6 Best Practices For Your End Users Terranova Security

New Sophisticated Email Based Attack From Nobelium Microsoft Security Blog

How To Prevent Data Breaches In 2021 12 Best Practices Paysimple
Data Protection Privacy And New Technologies European Union Agency For Fundamental Rights

Comments
Post a Comment